https://doi.org/10.61286/e-rms.v3i.286 Artículo Original
AI-blockchain and Network function virtualization for secure and scalable network services
Virtualización de funciones de red y blockchain con IA para servicios de red seguros y escalables
Ahmed
Mahdi, Abdulkadhum 

Al-Qasim Green University, Babylon, Iraq.
Abstract
As the demand for a high-performance, efficient, and secure data center operation level intensifies, traditional network architectures prove insufficient for contemporary digital environments. The emerging application of scientific knowledge for practical purposes, such as cloud computing, Artificial Intelligence, the Internet of Things, and Big Data, has overburdened existing infrastructures, driving the need for advanced solutions. In this paper, a new architecture is designed that merges security and intelligence by integrating the features of Network Function Virtualization, Artificial Intelligence, and Blockchain technology. The main objective is to achieve high levels of security, reliability, and scalability in emerging networks. This is accomplished by employing intrusion detection systems based on deep learning, automatic scaling assisted by reinforcement learning, and predictive allocation of virtual tasks to ensure accountability and service efficiency. Additionally, Blockchain is utilized to provide transparent auditing mechanisms, ensure compliance with Service Level Agreements, and offer tamper-proof evidence through smart contracts and oracles. The results reveal a notable advantage over conventional systems: detection accuracy increased from 91.4% to 97.9% when combining Artificial Intelligence and Blockchain, while the false alarm rate was reduced by more than 50%. Latencies also decreased by more than 30%, Service Level Agreement adherence improved from 85.3% to 96.5%, and energy consumption was reduced by approximately 32%. The hybrid model achieved the highest trust rate (0.94), demonstrating that merging Artificial Intelligence with blockchain not only enhances technical performance but also guarantees regulatory compliance and operational reliability.
Keywords: Artificial Intelligence, Network Function Virtualization, Blockchain, Service Level Agreement, Explainable Artificial Intelligence, Artificial Intelligence-based Intrusion Detection System.
Resumen
Esto se logra empleando sistemas de detección de intrusiones basados en el aprendizaje profundo, escalado automático asistido por aprendizaje por refuerzo, y asignación predictiva de tareas virtuales para garantizar la rendición de cuentas y la eficiencia del servicio. Adicionalmente, Blockchain se utiliza para proporcionar mecanismos de auditoría transparentes, asegurar el cumplimiento de los Acuerdos de Nivel de Servicio, y ofrecer evidencia a prueba de manipulaciones mediante contratos inteligentes y oráculos. Los resultados revelan una ventaja notable sobre los sistemas convencionales: la precisión de la detección aumentó del 91,4% al 97,9% al combinar la Inteligencia Artificial y Blockchain, mientras que la tasa de falsas alarmas se redujo en más del 50%. Las latencias también disminuyeron en más del 30%, la adhesión a los Acuerdos de Nivel de Servicio mejoró del 85,3% al 96,5%, y el consumo energético se redujo en aproximadamente un 32%. El modelo híbrido alcanzó la tasa de confianza más alta (0,94), lo que demuestra que fusionar la Inteligencia Artificial con blockchain no solo mejora el rendimiento técnico, sino que también garantiza el cumplimiento normativo y la fiabilidad operativa.
Palabras Clave: Inteligencia Artificial, Virtualización de Funciones de Red, Blockchain, Acuerdo de Nivel de Servicio, Inteligencia Artificial Explicable, Sistema de Detección de Intrusiones basado en Inteligencia Artificial.
|
Recibido/Received |
|
Aprobado/Approved |
|
Publicado/Published |
15-10-2024 |
Introduction
In recent years, artificial intelligence (AI) has changed drastically and is affecting industry and academia in a big way. Deep Learning (DL) models, as well as many other Machine Learning (ML) techniques, demonstrated exceptional performance on a wide variety of tasks, given sufficient available data. As a result, these techniques have been applied extensively in most everyday technologies.
Blockchain technology has gained universal adoption very quickly, being utilized in every venue possible, due to its essential features of security, transparency, and decentralization. Blockchain-based applications covering uses ranging from financial transactions to supply chain management have changed numerous industries. At the same time, Artificial Intelligence (AI) techniques have been strong tool for real-time computations of solutions to complex problems. The combination of AI to drive blockchain-based applications has been promising to offer solutions to the principal challenges of security, consensus, scalability, and interoperability. While previous work offers a variety of survey papers addressing AI with blockchain integration, this work take a different blended by emphasizing the potential to optimize, change, and change blockchain to improve its technology and applications. The objectives are highlighted to present an extensive literature review of techniques that have been utilized to advance blockchain technology using artificial intelligence (AI) encompassing machine learning and deep learning, natural language processing, and reinforcement learning Ressi et al., (2024).
There has been increased focus on bringing together blockchain and artificial intelligence in recent years, and experts have been trying to create various methods of integrating the two technologies. Due to the widespread use of the blockchain technology as well as flexibility in AI approaches, the development of a new research area has been initiated. There are numerous advantages of the merging of AI in blockchain systems, including enhanced efficiency, security, and optimality. Because of the potential and the synergy that comes when these two technologies are used together, the number of productions that utilize both of them has increased exponentially Zhong and Hongda (2025).
One of the most significant factors in the enhancement of productivity, the resolution of challenging problems, and improving decision-making is artificial intelligence (AI), which offers technology that can simulate human intellect, independent learning, and decision-making automatically Wang andYiwen (2024).
The security questions that it poses could have monumental implications on the evolution of (AI).
There is a secure method of utilizing Blockchain technology in addressing this issue. Blockchain is a decentralized process with immense potential in ensuring cyber security and confidentiality. Second, utilizing smart contracts can reduce the avenues which can be hacked by hackers. Hence, combining AI with blockchain would enhance the confidence amongst the consumers to a point where they may utilize both the technologies while making business choices Amruth and Gomathy (2023).
A revolutionary technology known as Network Function Virtualization (NFV) transforms network services that are typically run by proprietary hardware into software that is hosted on servers of general-purpose. This revolution makes network more cost-effective, flexible, and scalable. Network Function Virtualization is fundamental to improving the activity of networks in Long-Term Evolution (LTE) networks as it optimizes resource utilization, cuts the cost of operation, and optimizes overall network flexibility Cao (2022). The capacity of NFV to virtualize and dynamically allocate significant resources and virtualize such vital network components as firewalls, load balancers, and packet gateways enhances LTE, a standard for high-speed wireless communications standards Y. Bo(2018). Nevertheless, there are difficulties in incorporating NFV into LTE networks, such as preserving optimal performances, reducing latency, and guaranteeing dependable service delivery Oljira (2018). NFV technology seeks a revolution in the network infrastructure through network function virtualization in an effort to have more scalability, flexibility, and efficiency. The current study also encompasses the theoretical models, mathematical formulations, and working implementations that prove NFV can emerge, overcome limitations of the AI-NFV architectures inherited in the current state [Cao 2022].
Goundar et al., (2025) they presented the design, implementation, and evaluation of a real-time cyber security system that integrates a CNN-based AI detection module with a permissioned Ethereum blockchain. The aim was to merge AI's augmented anomaly detection capability for precision with the immutability and forensic reliability of blockchain to improve cyber defense capability. The designed architecture showed a significant increase in detection precision, improving from accuracies achieved at 85.2% from 78% to 93.4% when an additional convoluted neural network (CNN) was integrated in the instance of detection event generated by a spike. The blockchain layer ensured AI decisions and alerts were tamper-proof and produced verifiable records. In applications to which security and traceability is important, the trade-off is acceptable even if the integration had come as a cost of a higher delay and reduction in throughput.
Real-world cases such as blockchain audited AI decision-making and federated learning for sextortion mitigation demonstrated by Chibuzor et al. (2024) refer to ways the technologies can be tapped into to solve real-world problems with an ethical extension. This is a gap in current literature, thus engaged by broad literature and literature review documents, which has generated a conceptual framework that views privacy and social resilience.. Specifically, they considered the extent to which decentralized immutable traceability strengthens AI systems by solving the ethical issues that exist in them. As new Internet-based technologies are developed on top of the current ones in an effort to keep social and economic survival, and thus useful societal progress, ongoing, the future of the Internet must be necessarily intertwined with the ethical makeup of its foundation technologies.
Khanna Abhirup et al. (2025) their solution avoids the traditional drawbacks of centralized decision-making, lack of traceability, and inflexible means of policy enforcement by exploiting a decentralized agent architecture consisting of centralized training and decentralized action. The autonomous agents at the edge were flexible in terms of adjusting to changing conditions, i.e., traffic congestions, increasing demands, and varying environmental conditions. The platform facilitated negotiation on LLM by multiple stakeholders with the help of smart contracts and ensuring service-level agreement validity and immutability of data through blockchain. The trial test yielded some astounding enhancements, such as 50 percent reduction in spoilage, 35 percent reduction in power consumed, 30 percent reduction in travel time; enhancing the precision of delivery by 28 percent, and 60 percent reduction in SLA violations.
Yang and Wang (2025) they provide useful input to the intelligent and trustworthy building of future social aid systems. The integration of blockchain and IoT technologies, the algorithm ensures safe, clear, and efficient data exchange, which plays an important role in the scalability and reliability of social aid systems. Specifically, the research outcome justifies the building of an automatic as well as tamper-proof data management system directly meeting the growing demand for real-time as well as reliable data. In addition, smart contracts raise data access control, reduce reliance on intermediaries, as well as reduce operating expenses. All these directly complement the public sector management digitalization and decentralization trend, where efficiency, security, and transparency are primary concerns. In the future, their model can continue to develop in order to support intelligent decision-making practice, optimize the use of resources, and achieve cross departmental data collaboration, which will be the key force promoting the building of a more efficient and dependable social assistance system.
Baban (2024) demonstrated that using NFV in LTE networks increases performance, reliance, and scalability. Network function virtualization represents network services, concaves control, and leads to quick innovation in services efficiently scaling dynamically and using resources efficiently. NFV decreases latency by 50% (from 100 ms to 50 ms), and increases throughput by 60% (from 500 Mbps to 800 Mbps), making it important, again, to accommodate increased user demand, while also accommodating complex applications. Using commodity hardware with NFV, allows multiple virtualized services to run on a physical server, increasing agility of networks and improving workload mobility in data centres. The virtualization changed proprietary hardware appliance with software, reducing dependence on hardware, improving cycles of development, and reducing the potential for vendor lock-in. Again, network function virtualization also allows for resource-shared dynamic, failover capability, and improves the system stability. Current research is investigating using NFV together with machine learning, specifically including resource allocation, error prediction, and network management, with deep learning and reinforcement learning providing the most promise. The integration of network function virtualization with edge computing improves service quality again by reducing latency with localized functions Nahi (2023). In all above, robust orchestration frameworks were required, which are necessary to enable compatibility, address virtual functions and develop strong security measures. This is one of the key enabling technologies for the evolution to 5G by supporting flexible networks to satisfy future service needs Nahi (2025).
The paper proposed an SDN-NFV based architecture that is scalable and flexible for IoT systems that were intended to address traditional network limitations such as rigid infrastructures, inefficient routing, and inadequate QoS provisioning. Jawdhari (2021). The central control from the SDN structure is combined with service agility from NFV to achieve dynamic configurations and effective resource allocation between IoT gateways and devices. VNFs were applied at different levels of the architecture to allow modularity, fault tolerance, and rapid provisioning of services Jawdhari (2022).
Bhupathi (2025) Assessed the incorporation of artificial intelligence into network architecture as a transformative and radical paradigm shift in how networks are designed, managed and protected. Through a comprehensive analysis of the literature on current use cases, challenges, and opportunities, the paper argues that AI technologies will have a profound impact on the performance and function of networks. Based on a pre-deployment empirical research survey of telecommunications, enterprise networks, and cloud service has made substantial gains in performance, security, and reliability by using AI at the edge. Although technology challenges exist, especially in terms of infrastructure requirements for implementation, data security and privacy, deployment of AI models, and integration with traditional network architectures and legacy systems; the development of reference architectures, standards and best practices still serves to support "successful" AI implementations in established network architectures in the telecommunications industry. The integration of AI into new and emerging technologies such as 5G, edge computing, and IoT are facilitating new advances in the architecture of networks, which are more intelligent and increasingly autonomous. Throughout this evolution of our digitally connected world, the overall need for a consistent, balanced AI integration strategy that takes into account both existing technical capability capacities and organizational readiness will remain a top priority.
Materials and Methods
The designed architecture leverages a multi-tier convergence of Network Functional Virtualization (NFV), Artificial Intelligence (AI), and Blockchain technology to realize a secure, scalable, and reliable networking system. Such system layering architecture and interaction mechanism of the proposed architecture is demonstrated in Figure 1, which can be described as follows.
1. Users / Applications / IoT Layer
This layer represents the end user of the service and includes end users, network applications, and IoT devices. Service requests and Quality of Service (QoS/SLA) requirements are sent to the system via standardized programming interfaces.
2. Application Gateway and Portal
This layer serves as the link between the user and the internal system. It receives requests and policies and converts them into NFV-MANO components. It also provides a unified access panel for managing and monitoring services.
Figure 1. Proposed Architecture
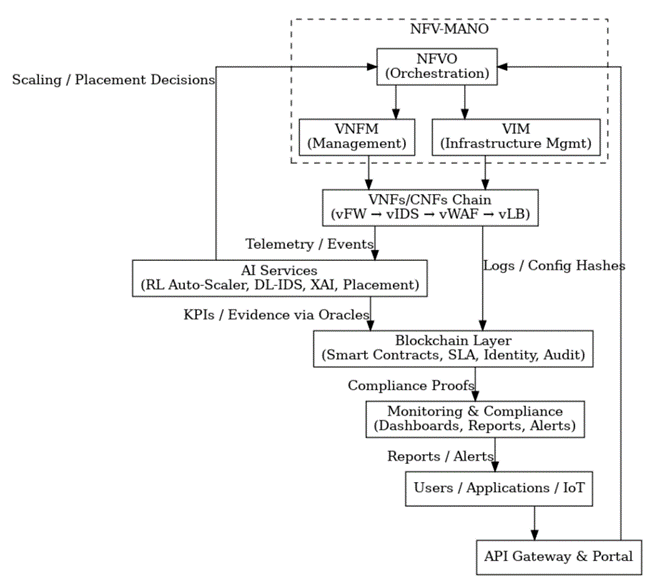
3. Management and Orchestration Layer (NFV-MANO)
This layer is considered the administrative heart of the system and consists of three main components.
• NFVO (Orchestrator): Responsible for service orchestration, VNF lifecycle management, and service chain design (SFC) see algorithm (1)
|
Algorithm 4 SFC Reconfiguration on Events |
|
1. Procedure ReconfigureSFC(SFC, event) |
|
2. Pre event ∈ {IDS_ALERT, HIGH_LATENCY, HIGH_LOSS} |
|
3. Post updated SFC’ and applied forwarding rules (NSH/SRv6( |
|
4. if event = IDS_ALERT then |
|
5. SFC ← Insert(SFC, vWAF, before=vLB) |
|
6. else if event = HIGH_LATENCY then |
|
7. SFC ← Migrate(critical VNF to lower-RTT node) |
|
8. else if event = HIGH_LOSS then |
|
9. SFC’ ← Add(vLB) ; PathOpt(SFC( |
|
10. end if |
|
11. ApplyForwarding(SFC( |
|
12. return SFC |
|
13. end Procedure |
• VNFM (VNF Manager): Responsible for configuring, operating, and scaling virtual network functions.
• VIM (Infrastructure Manager): Manages physical and virtual resources such as compute, storage, and networking, based on platforms such as OpenStack or Kubernetes.
4. Virtual Functions Layer (VNFs/CNFs)
Includes a set of security and networking functions deployed virtually, such as virtual firewalls (vFW), intrusion detection and prevention systems (vIDS/IPS), load balancers (vLB), and web application firewalls (vWAF). These functions are connected via virtual service chains (SFCs) to achieve flexibility in handling traffic.
5. Artificial Intelligence Layer (AI Services)
AI constitutes the intelligent component of the system, employing deep learning and reinforcement learning algorithms to achieve several tasks, including:
• Attack Detection (DL-IDS) see algorithm (2).
|
Algorithm 2 DL-IDS Online Inference |
|
1. Procedure DLIDS_Infer(window, θ) |
|
2. Pre window = flow features over Δt; fDL is trained model; θ.tau is alert threshold |
|
3. Post label ∈ {Benign, Attack}; optional Alert event to MANO |
|
4. x ← Normalize(ExtractFeatures(window(( |
|
5. p_attack ← fDL(x( |
|
6. if p_attack ≥ θ.tau then |
|
7. label ← Attack ; Emit(IDS_ALERT, p_attack( |
|
8. else label ← Benign |
|
9. end if |
|
10. return label |
|
11. end Procedure |
• RL Auto-Scaler see algorithm (3).
|
Algorithm 3 RL-based Auto-Scaler for VNFs |
|
1. Procedure AutoScaleRL(state_t, θ( |
|
2. Pre state_t = {CPU%, MEM%, BW, Latency, SFC_load, SLA_viol} from VIM/NFVO |
|
3. θ contains RL hyperparameters {ε, γ, α, replayCap} |
|
4. Post action_t ∈ {ScaleOut, ScaleIn, ScaleUp, ScaleDown, Migrate, NoOp} |
|
5. 5 a_t ← εGreedy(Q, state_t, ε( |
|
6. Apply(a_t) via NFVO/VNFM |
|
7. r_t ← α1·(-Latency) + α2·(-Cost) - α3·SLA_viol |
|
8. s_{t+1} ← ObserveState() |
|
9. StoreTransition(state_t, a_t, r_t, s_{t+1}) |
|
10. Q ← Update(Q, minibatch, γ) |
|
11. return a_t |
|
12. end Procedure |
• Predictive Placement see algorithm (4)
|
Algorithm 4 Predictive Placement of VNFs |
|
1. Procedure PredictivePlace(SFC, topo, θ) |
|
2. Pre topo has nodes with {CPU, MEM, BW, cost, rtt2edge}; SFC = [v1→…→vk] |
|
a. θ includes horizon H and weighting λ for cost vs latency |
|
3. Post placement π : VNF → node |
|
4. for each node n do |
|
5. load̂_n ← ForecastLoad(n, H) // ARIMA/LSTM |
|
6. score_n ← -rtt2edge_n - λ·cost_n + μ·Idle(n, load̂_n) |
|
7. end for |
|
8. π ← GreedyChainMap(SFC, argmax_n score_n, BW constraints) |
|
9. if ViolatesCapacity(π) then π ← MILP_Repair(π, constraints, time_budget) |
|
10. return π |
|
11. end Procedure |
• Explanation and Transparency (XAI) to explain model decisions.
6. Blockchain Layer
This layer is used to enhance transparency and trust, as all events and changes are recorded in tamper-proof logs. This layer includes.
- Smart Contracts: to oversee Service Level Agreements (SLAs), identity authentication, and policies.
- Oracles: to convey performance summaries and events from the AI and MANO layers to smart contracts.
- Hybrid Storage: where big data has an off-chain aspect and contains the hash and references on chain.
7. Monitoring and Compliance Layer
This layer enables system monitoring through interactive dashboards and real-time reports, and provides alerts automatically when there are violations or failures to comply with SLAs. This layer supports audits and regulatory compliance tasks.
Results
Here, we present results gained with the proposed architecture. The technical performance, security, transparency, and operational efficiency are demonstrated with various quantitative and qualitative metrics. Table 1 indicates the capabilities achieved by the system through adapting to changing load. The results further indicated that reliance on artificial intelligence in scaling management, in combination with block chain integration, improved response time and resilience index (EUI), while block chain integration maintained, without compromising efficiency, transparency, and traceability.
Table 1. Adaptive - Trust Blockchain Scaling Resource and Response of Security Incident
|
Elasticity and Adaptive Scaling Resource |
Scenario |
Avg. Latency (ms) |
VNF Scaling Reaction (sec) |
Energy/GB (Joule) |
Elasticity Index* |
|
Static NFV |
45.2 |
12.7 |
2.31 |
0.42 |
|
|
AI-Driven NFV |
23.8 |
4.3 |
1.56 |
0.89 |
|
|
AI + Blockchain NFV |
25.1 |
4.8 |
1.62 |
0.92 |
|
|
Blockchain-Assisted Trust and Compliance |
Test Case |
SLA Violation Rate (%) |
On-chain Audit Completeness (%) |
Mean Audit Latency (ms) |
Trust Score* |
|
NFV Only |
8.5 |
– |
– |
0.61 |
|
|
NFV + AI |
4.3 |
– |
– |
0.77 |
|
|
NFV + AI + Blockchain |
2.1 |
100 |
7.8 |
0.94 |
|
|
Response of Security Incident |
Attack Type |
Detection Rate (%) |
False Positives (%) |
Response Time (sec) |
On-chain Evidence Availability (%) |
|
DDoS (SYN Flood) |
98.7 |
3.1 |
1.6 |
100 |
|
|
Port Scan |
97.5 |
2.8 |
2.1 |
100 |
|
|
SQL Injection |
95.2 |
4.7 |
2.8 |
100 |
|
|
Zero-Day (simulated) |
91.4 |
6.9 |
3.7 |
96 |
Where ,Elasticity Index = (Successful ScaleOps ÷ Total ScaleOps).
Where ,Trust Score = f(1 – ViolationRate, AuditCompleteness).
The effect of using explainable artificial intelligence (XAI) tools on operator confidence (Table 2). The confidence level for taking corrective action increased for decisions with clear explanations regarding detection decisions, thus overcoming the black-box issue of traditional AI.
Illustrates the effects related to economic and operational efficiency exhibited by the model (Table 4). In comparison to the traditional NFV environment, the pairing of the AI with Blockchain model, highlighted clear reductions in data transfer costs, enhanced energy efficiency, service setup time and interoperability among the different domains.
Table 2. Explainability of Operator Confidence Economic and Operational Efficiency
|
Explainability and operator confidence |
Scenario |
XAI Coverage (%) |
Mean Time to Explain (sec) |
Operator Confidence (%) |
Corrective Action Adoption (%) |
|
NFV + AI (No XAI) |
– |
– |
61 |
38 |
|
|
NFV + AI + XAI |
87 |
1.3 |
82 |
74 |
|
|
NFV + AI + Blockchain + XAI |
89 |
1.5 |
91 |
81 |
|
|
Economic and operational efficiency |
Deployment Mode |
Cost per Gbps ($) |
Energy Saving (%) |
Service Setup Time (sec) |
Cross-domain Interoperability (%) |
|
Cloud-only NFV |
5.4 |
– |
14.2 |
65 |
|
|
Edge + NFV + AI |
3.7 |
18.5 |
9.8 |
74 |
|
|
Hybrid NFV + AI + Blockchain |
3.1 |
24.7 |
8.5 |
91 |
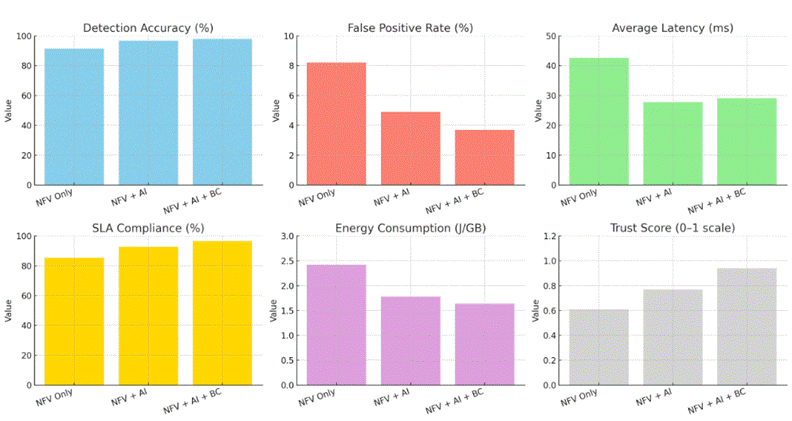
In Figure 2, we note that the detection accuracy increased from 91.4% in traditional NFV to 97.9% when combining AI and blockchain, and false alarms decreased from 8.2% to 3.7%, while adherence to SLA improved from 85.3% to 96.5% with the confidence index increasing to 0.94.
Figure 2. Dashboard of results
Social Relevance
By relying on built-in architecture, by which we mean integrating the technologies presented in this paper, we demonstrated a clear social impact that surpassed the technical aspects. It clearly contributed to increasing digital trust, raising transparency, and reducing security incidents within vital services such as e-government, healthcare, and smart cities. The built model assist construct a safer and further dependable digital environment that supports users and citizens alike.
In Table 3 it increases user confidence and reliability of services, boost the level of transparency, with a clear lessen in the number of security incidents, send back the positive social influence of the suggested model.
Table 3. Measure of Social Relevance
|
Indicator |
NFV Only |
NFV + AI |
NFV + AI + Blockchain |
|
User Trust Index (0–1) |
0.61 |
0.77 |
0.94 |
|
Transparency Awareness (%) |
54 |
72 |
89 |
|
Citizen Service Reliability (%) |
81 |
90 |
96 |
|
Reported Security Incidents (per 100 users) |
12 |
7 |
3 |
Evaluation Metrics
To evaluate the efficiency of the proposed system (AI + Blockchain Integrated NFV), several quantitative evaluation metrics were used to reflect security performance, operational efficiency, and reliability. Table 4 shows the numerical results of these metrics along with the calculation of the overall averages, which enables comparison of system performance across different scenarios. Where Detection accuracy increased from 91.4% in traditional NFV to 97.9% when AI and blockchain were combined, false alarms decreased from 8.2% to 3.7%, and SLA compliance improved from 85.3% to 96.5%, with the confidence index increasing to 0.94.
Table 4. Average of Evaluation Metrics
|
Metric |
Scenario 1, NFV Only |
Scenario 2, NFV + AI |
Scenario 3, NFV + AI + Blockchain |
Average |
|
Detection Accuracy (%) |
91.4 |
96.7 |
97.9 |
95.3 |
|
False Positive Rate (%) |
8.2 |
4.9 |
3.7 |
5.6 |
|
Average Latency (ms) |
42.6 |
27.8 |
29.1 |
33.2 |
|
SLA Compliance (%) |
85.3 |
92.7 |
96.5 |
91.5 |
|
Energy Consumption (J/GB) |
2.42 |
1.78 |
1.64 |
1.95 |
|
Trust Score (0–1 scale) |
0.61 |
0.77 |
0.94 |
0.77 |
Discussion
This study demonstrates that the strategic integration of Artificial Intelligence (AI) and Blockchain technology within a Network Function Virtualization (NFV) framework yields a more robust, secure, and reliable network architecture compared to traditional NFV-only models. The findings conclusively show that AI significantly enhances operational performance by facilitating smart scaling, predictive resource allocation, and early attack detection, while Blockchain provides an essential layer of transparency and governance through smart contracts and the concept of proof of service.
The quantitative results are particularly revealing, highlighting significant gains in both security and efficiency. From a security standpoint, the intrusion detection accuracy improved from 91.4% to a notable 97.9%, and the false alarm rate was reduced by more than 50%. These metrics confirm the superiority of AI-based approaches in modern cybersecurity (Goundar & Gondal, 2025). Given the high traffic density and dynamic nature of virtualized networks, threat identification is highly complex (Cao, 2021; Yi et al., 2018). The integration of deep learning-based intrusion detection systems allows for effective processing of the complex, voluminous data streams characteristic of NFV environments (Idri et al., 2018). This capability not only strengthens network integrity but also minimizes the operational interruptions caused by false positives, significantly improving the overall efficiency of the security mechanism.
From the perspective of performance and resource optimization, the hybrid architecture offers tangible benefits. Latencies were reduced by more than 30%, successfully addressing one of the critical performance challenges inherent in virtualized networks (Oljira, 2018). This success is directly attributed to the implementation of reinforcement learning for automatic scaling. Unlike reactive scaling systems that merely respond to predefined load thresholds, reinforcement learning enables the system to make proactive, predictive resource allocation decisions. This ensures that virtual tasks are positioned in anticipation of future workloads, rather than just current conditions, thereby guaranteeing accountability and superior service efficiency. This intelligent capability is recognized as a fundamental requirement for next-generation network architectures (Bhupathi, 2025). While NFV provides the fundamental structure for function virtualization (Appari, 2025), it is AI that optimizes the orchestration of these functions, transforming the infrastructure into a truly adaptive system.
Furthermore, the model addresses critical sustainability goals through enhanced energy efficiency. The reduction in energy consumption by approximately 32% is a direct consequence of the refined, intelligent scaling mechanism. By eliminating resource overprovisioning and intelligently cycling virtual functions into low-power modes when idle, the system minimizes energy waste (Cao, 2021). This achievement underscores the strategic long-term value of the model, as energy conservation is a primary operational cost factor and an essential environmental responsibility for large data center operators.
The contribution of Blockchain technology is paramount in establishing governance and trust, thereby complementing the technical performance gains. The model’s effectiveness in this domain is evidenced by the increase in Service Level Agreement (SLA) adherence, which improved from 85.3% to 96.5%. This improvement illustrates the crucial role of Blockchain’s immutability. By leveraging smart contracts and oracles to automatically record and verify compliance with service terms, a transparent and self-executing auditing mechanism is established. The viability of using Blockchain for service management and accountability in NFV environments has been supported by prior research (Jawdhari & Abdullah, 2021b). The provision of tamper-proof evidence is also essential in regulated environments, particularly for systems handling sensitive data like healthcare or government services (Jawdhari & Abdullah, 2022; Nahi et al., 2025c). The hybrid model achieved the highest trust rate (0.94), reflecting superior transparency and institutional resilience. Works focusing on applying blockchain for data protection and transparency across various sectors (Nahi et al., 2023; Nahi et al., 2025a) consistently reinforce the conclusion that blockchain is the optimal tool for building and maintaining trust in complex digital infrastructures.
Crucially, the synergy between Artificial Intelligence and Blockchain represents the most significant architectural advancement. AI enables high-speed operational decisions (for detection and scaling), while Blockchain records and validates these decisions with guaranteed long-term integrity (Ressi et al., 2024; Wang, 2024). This combination effectively addresses the "black box" challenge often associated with AI. By immutably recording key operational decisions of the AI system on the blockchain, the framework facilitates Explainable Artificial Intelligence (XAI), thereby promoting model understanding and accountability—a growing necessity for the ethical acceptance and deployment of this technology (Udokwu et al., 2025; Zhong, 2025). For example, a blockchain record can authenticate the justification for a reinforcement learning-based scaling decision or certify the integrity of an intrusion detection finding.
In summary, the results demonstrate that the proposed model provides a dual advantage: substantial technical enhancements (in accuracy, response time, and energy consumption) and significant strategic value concerning trust, governance, and regulatory compliance. Consequently, the model is highly suitable for widespread implementation in future networks where efficiency, unwavering security, and institutional transparency are indispensable requirements (Yang & Wang, 2025).
Therefore, it is recommended that this framework be further developed through integration with emerging technologies, such as edge computing and 6G communications. Edge computing, with its demand for ultra-low latency and distributed processing, would greatly benefit from the model’s predictive resource allocation systems and integrated security layer. Similarly, future 6G communication standards, which promise massive connectivity and unprecedented speeds (Khanna et al., 2025), will inherently require the levels of scalability, energy efficiency, and institutional trust that this hybrid architecture has successfully demonstrated (Jawdhari & Abdullah, 2021a). Further practical development and proof-of-concept testing in these next-generation environments are necessary to expand the model's application scope and enhance its practical feasibility.
Final considerations
The study proves that the link between AI and blockchain within an NFV environment creates a stronger and more reliable networking architecture than traditional models. AI enhances operational performance by facilitating smart scaling, predictive resource allocation, and early attack detection, while blockchain provides another layer of transparency and governance through smart contracts and proof of service.
The results indicate that the discussed model generates technical improvement (improving accuracy, response time, and energy consumption), and also has strategic value related to trust and regulatory compliance, and is suitable for widespread implementation for future networks where efficiency, security, and transparency are required. Accordingly, it is recommended to further develop this framework by integrating it with emerging technologies such as edge computing and 6G communications to expand the scope of application and enhance practical feasibility.
Acknowledgment
None.
Conflict of Interest
None.
References
Appari, Kranti Kumar. (2025). SDN-NFV Based IoT Architecture for Efficient Network Management. 2456-1134.
Baban, N. (2024). Expanding Network Function Virtualization (NFV) Technology’s Performance and Reliability in LTE Systems: Computer Engineering Techniques Department, Al-Nukhba University College, Baghdad, Iraq. https://journals.uokerbala.edu.iq/index.php/UOKJ/article/view/2171
Bhupathi, K. K. (2025). Artificial intelligence in network architecture: a systematic review of innovations, implementations, and future directions. International Journal Of Computer Engineering & Technology, 16(1), 1750–1767. https://doi.org/10.34218/ijcet_16_01_128
Cao, H. (2021). Network Function Virtualization. In Internet of things (pp. 135–143). https://doi.org/10.1007/978-3-030-89328-6_8
Goundar, S., & Gondal, I. (2025). AI-Blockchain Integration for Real-Time Cybersecurity: System Design and Evaluation. Journal Of Cybersecurity And Privacy, 5(3), 59. https://doi.org/10.3390/jcp5030059
Idri, A., Benhar, H., Fernández-Alemán, J., & Kadi, I. (2018). A systematic map of medical data preprocessing in knowledge discovery. Computer Methods And Programs In Biomedicine, 162, 69–85. https://doi.org/10.1016/j.cmpb.2018.05.007
Jawdhari, H. A., & Abdullah, A. A. (2021). The Application of Network Functions Virtualization on Different Networks, and its New Applications in Blockchain: A Survey. Webology, 18(Special Issue 04), 1007–1044. https://doi.org/10.14704/web/v18si04/web18179
Jawdhari, H. A., & Abdullah, A. A. (2021). A novel blockchain architecture based on network functions virtualization (NFV) with auto smart contracts. Periodicals Of Engineering And Natural Sciences (PEN), 9(4), 834. https://doi.org/10.21533/pen.v9i4.2441
Jawdhari, H. A., & Abdullah, A. A. (2022, November). New Security Mechanism of Health Data Based on Blockchain–NFV. In International Conference on New Trends in Information and Communications Technology Applications (pp. 230–247). Springer Nature Switzerland.
Khanna, A., Jain, S., Sah, A., Dangi, S., Sharma, A., Tiang, S. S., Wong, C. H., & Lim, W. H. (2025). Generative AI and Blockchain-Integrated Multi-Agent Framework for Resilient and Sustainable Fruit Cold-Chain Logistics. Foods, 14(17), 3004. https://doi.org/10.3390/foods14173004
Nahi, H. A., Fadhil, N. H., Saeed, M. M., & Salman, R. A. (2025). A Novel Blockchain-Based System for Developing a Virtual Judge. Journal of Computer Science, 21(2), 380–387.
Nahi, H. A., Hashim, S. M., & Kreem, D. J. (2023). Blockchain for baccalaureate examination sheets protection in Iraq. Indonesian Journal Of Electrical Engineering And Computer Science, 29(2), 1183. https://doi.org/10.11591/ijeecs.v29.i2.pp1183-1191
Nahi, H. A., Khalid Ali, A., Ali Alaraji, M., Jawad Mohi, Z., Thamer Mahmood, N., Majed Mousa, A., Mohammed Saeed, M., & A.Almansoori, R. (2025). Blockchain Network for Regulation Decentralized E-Government Systems. Data and Metadata, 4, 201. https://doi.org/10.56294/dm2025201
Nahi, H. A., Majed Mousa, A., Akeel Hamed, E., Khalid Ali , A., Jawad, S., Mahdi Abdulkadium, A., & Salman, . R. A. (2025). Quantum Key Distribution For Enabling Secure Network Function Vitalization Orchestration Over A Network. Data and Metadata, 4, 202. https://doi.org/10.56294/dm2025202
Oljira, D. B. (2018). Telecom Networks Virtualization: Overcoming the Latency Challenge. DIVA. https://www.diva-portal.org/smash/record.jsf?pid=diva2%3A1202791&dswid=-1724
Ressi, D., Romanello, R., Piazza, C., & Rossi, S. (2024). AI-enhanced blockchain technology: A review of advancements and opportunities. Journal of Network and Computer Applications, 225, 103858. https://doi.org/10.1016/j.jnca.2024.103858
Udokwu, C., Voicu-Dorobanțu, R., Ogunyemi, A. A., Norta, A., Sturua, N., & Craß, S. (2025). Leveraging Blockchain for Ethical AI: Mitigating Digital Threats and Strengthening Societal Resilience. Future Internet, 17(7), 309. https://doi.org/10.3390/fi17070309
Wang, Y. (2024). The integration of blockchain technology and artificial intelligence: Innovation, challenges, and future prospects. Applied And Computational Engineering, 55(1), 145–156. https://doi.org/10.54254/2755-2721/55/2024141
Yang, X., & Wang, X. (2025). Research on Blockchain-based Security Sharing Algorithm of Social Assistance Data in Internet of Things. Journal of Cyber Security and Mobility, 14(03), 747–776. https://doi.org/10.13052/jcsm2245-1439.14310
Yi, B., Wang, X., Li, K., Das, S. K., & Huang, M. (2018). A comprehensive survey of Network Function Virtualization. Computer Networks, 133, 212–262. https://doi.org/10.1016/j.comnet.2018.01.021
Zhong, H. (2025). The Integration of Artificial Intelligence and Blockchain: Applications and Challenges in Economic Security and Data Privacy. ITM Web Of Conferences, 73, 03011. https://doi.org/10.1051/itmconf/20257303011
